Mishaal Rahman / Android Authority
TL;DR
- Google may be cracking down on a known Android security attack method in Android 15.
- Malicious apps that can read your notifications can intercept one-time passwords (OTPs) and hijack your accounts, and Google wants to prevent this.
- Code within Android 15 suggests Google might stop untrusted apps from reading notifications with OTPs.
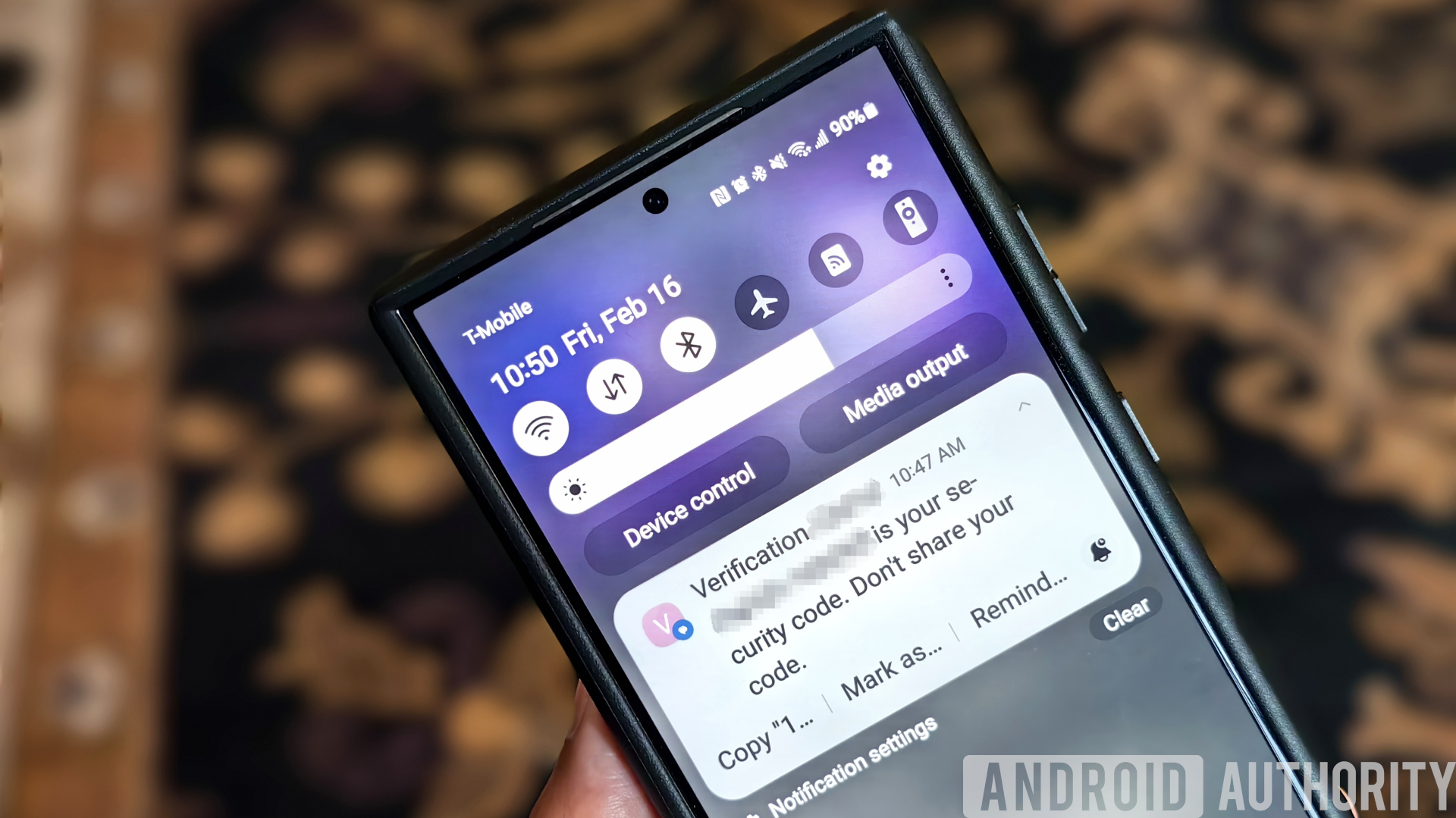
It’s essential to protect your online accounts so they don’t fall into the hands of hackers, which is why you should use a passkey or enable two-factor authentication (2FA) whenever possible. While some forms of 2FA are more secure than others, some platforms only support the most basic methods, wherein your one-time passwords (OTPs) are sent via email or text. These methods are convenient since they don’t require additional setup, but they are also less secure since they’re easier to intercept. Fortunately, Android 15 might be adding a new feature that prevents your OTPs from being read by malicious Android apps.
While digging through the Android 14 QPR3 Beta 1 update, I discovered the addition of a new permission named RECEIVE_SENSITIVE_NOTIFICATIONS. This permission has a protectionLevel of role|signature, which means it can only be granted to applications with the requisite role or to applications that the OEM signs. While the exact role that grants this permission hasn’t been defined yet, it’s likely that Google doesn’t intend to open this permission up to third-party apps.
<permission android:name="android.permission.RECEIVE_SENSITIVE_NOTIFICATIONS" android:protectionLevel="role|signature"/>
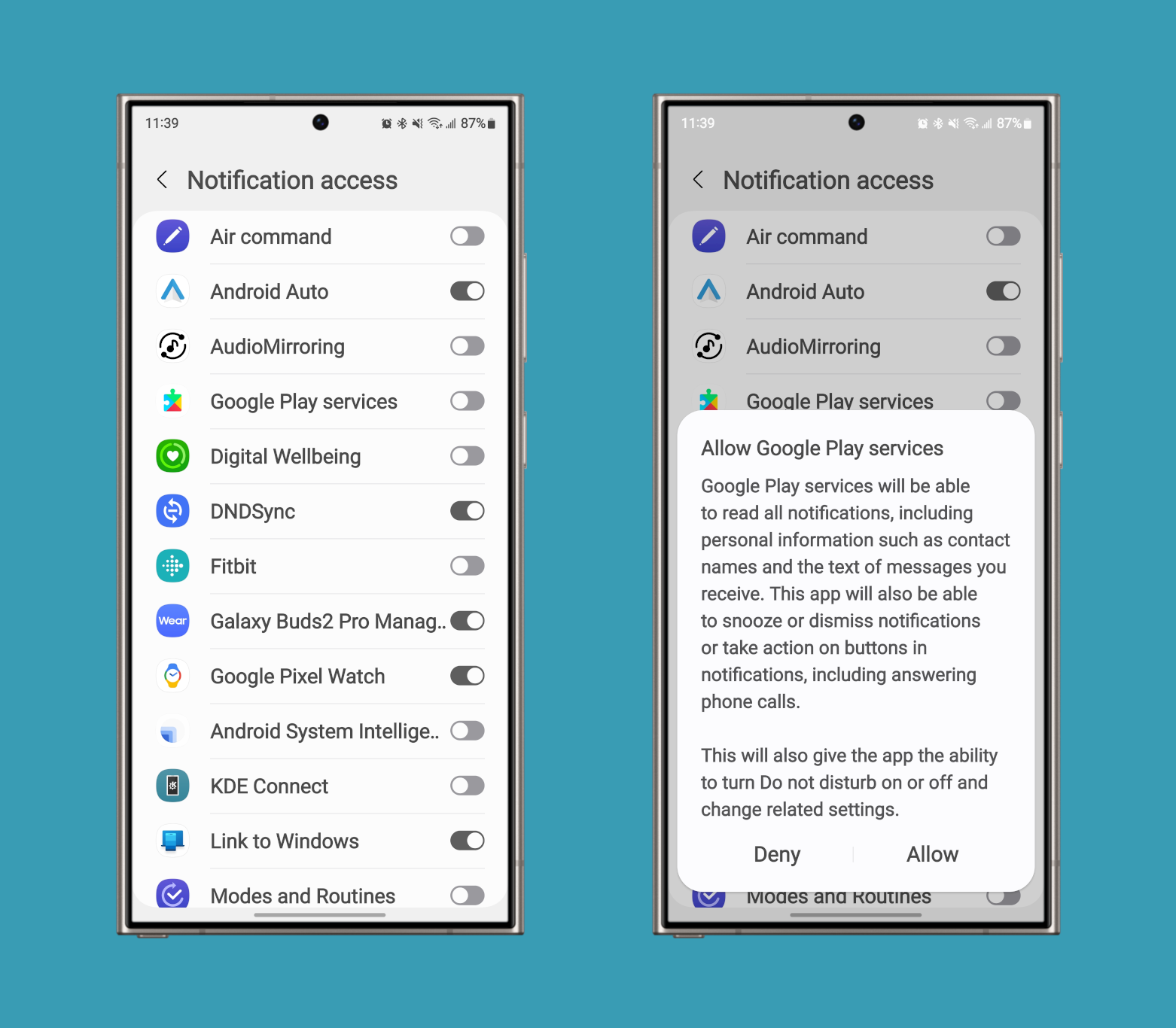
As for why I believe that, it’s because this permission is tied to a new, in-development platform feature that aims to redact sensitive notifications from untrusted apps that implement a NotificationListenerService. This is an API that lets apps read or take action on all notifications. Users need to manually grant apps permission in Settings before the NotificationListenerService API becomes available, though.
Mishaal Rahman / Android Authority
Notification access settings in Android 14 on a Galaxy S24 Ultra.
Given how powerful this permission and API are, it’s no surprise that Google would want to limit the kind of data that apps can get from them. We don’t know precisely what constitutes an “untrusted” app, but it’s likely any apps that don’t hold the new RECEIVE_SENSITIVE_NOTIFICATIONS permission. This permission would probably only apply to select system apps.
We also don’t know exactly what kinds of notifications Google thinks are “sensitive,” but we have reason to believe they’re referring to notifications with 2FA codes. While digging through the source code for Android 14, we discovered a new flag called OTP_REDACTION that is used to gate “the redaction of OTP notifications on the lock screen.” This flag is currently unused in Android 14, though, as it’s likely something that Google intends to release with Android 15.
With the addition of the OTP_REDACTION flag and the RECEIVE_SENSITIVE_NOTIFICATIONS permission, Android will have three ways to protect users from leaking their 2FA codes to third parties. The OTP_REDACTION flag suggests that Android will stop users from leaking their 2FA codes on the lock screen, while the RECEIVE_SENSITIVE_NOTIFICATIONS permission suggests that Android will stop untrusted apps from reading notifications with 2FA codes. Finally, an existing feature from Android 13 blocks users from enabling an app’s notification listener service if it was installed from an untrusted source.








